
If you've always been curious about how blockchain works but couldn't find a clear answer anywhere, this article is for you. We tried to explain the subject in a way that even your granny 👵 would understand.
Let's start with a short and simple explanation and then dive in.
Cryptocurrency is virtual money that exists only online. It has no paper equivalent. People don't need any bank to conduct cryptocurrency transfers; it is truly decentralized, and there is no single watchdog involved in the system. Instead there is a blockchain, that is a technology that secures data storage. Information in a blockchain cannot be changed or faked because it is first encrypted and then stored on thousands of devices around the world.
That is why you will not be able to add a couple of millions on your account or transfer the same coins on two different wallets: the system will compare data with the stored information and immediately recognize the scam. Consensus is responsible for this.
Decentralization gives us the most reliable, fair, unprincipled, incorruptible, and independent way of storing data, which can potentially be used everywhere:
🕴 in politics (fair elections),
📑 in governmental systems (taxes, healthcare),
💼 and in business (logistics, sales).
Now let's learn how it works. Fasten your belts, because difficulty is going to increase.
What is blockchain
As we have already mentioned, blockchain is a data storage technology. The term comes from ‘block’ and ‘chain’. Combining two words, we get ‘chain of blocks’. What are the blocks? 🤔
Imagine that you are moving to another city. You need boxes. And you need to pack your staff as compact as possible to use a minimum of space and fit a maximum of items. So you save money on boxes, packages, bubble wrap, and delivery because the movers' bill is going to be less expensive.
While packing things in boxes, you will probably sign them so that they do not get lost during transportation, and this step will help you understand where every single item is located during unpacking.
The logistics company will also mark them. Sticks can be scanned to find out who owns them and what their direction is. So logisticians will be able to track its movement and provide evidence if needed.
Blockchain works almost like a logistics company. 😬
How does blockchain works
The blockchain's general aim is to offer people an almost perfect way to store data.
📦 Blockchain consist of blocks. Developers can settle their size during the cryptocurrency coding process. For example, the Bitcoin blockchain's block size is about 1 MB.
This metric is dynamic. It depends on a number of factors, including the workload and fee level. Metric's growth makes blocks expand. For instance, during bitcoin's fee growth in spring 2023, the block size reached 2.6 MB. Anyway, in its normal condition, the block size is about 1 MB.
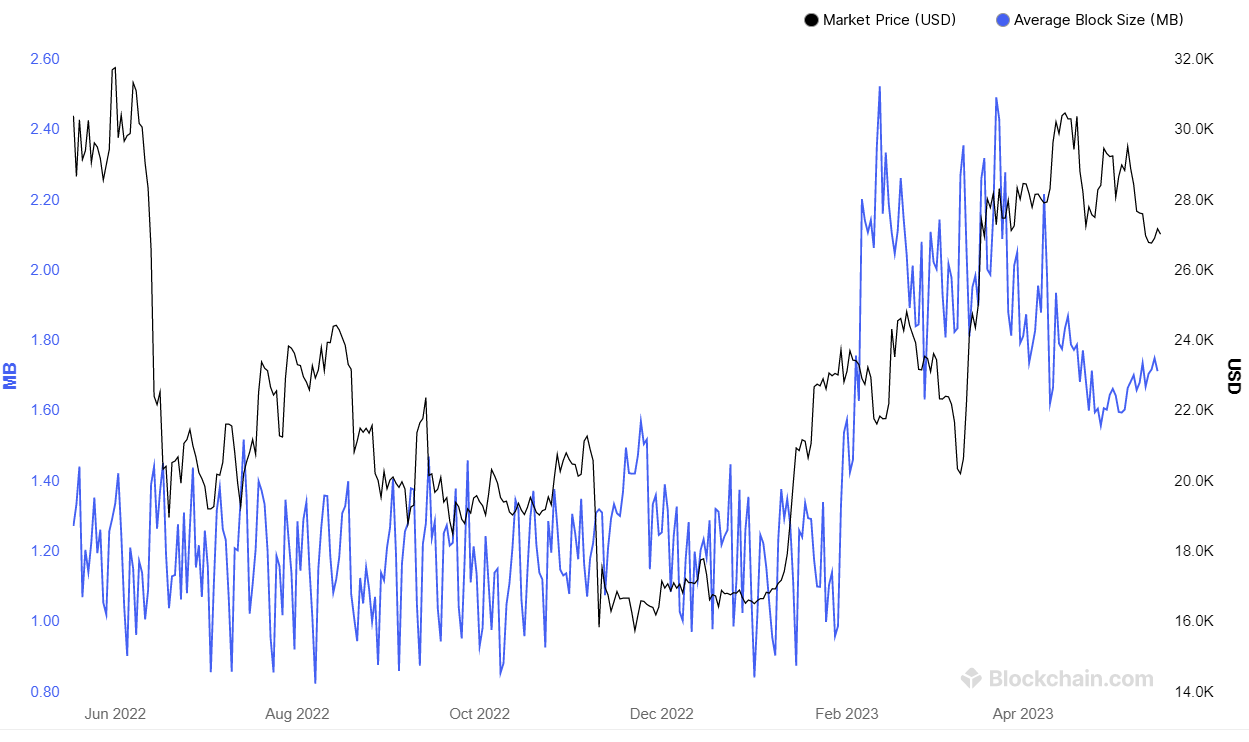
The size of blocks in the bitcoin blockchain. Source: blockchain.com.
🖇 All blocks in the blockchain are connected by a "glue" of information. And now let’s get acquainted with the hash tree or Merkle tree algorithm. It converts a large amount of information into a small line of code, which is needed to "link" a block to the next one.
Let's see how the hash tree works in the example pictured on the scheme below:
📃 We have four records: A, B, C, and D. Let's say these records provide information about four transactions that need to be placed in a block.
🧮 The system hashes each of the records and converts them into a unique set of characters. So we get four hashes: hash A, hash B, hash C, and hash D.
🔗 Now we need to split the received hashes into pairs. Let's take hash A plus hash B and hash C plus hash D. Each pair of hashes brings us one new hash:
☝️ hash E = (hash A + hash B);
✌️ hash F = (hash C + hash D).
Thus, we have converted four original records into two.
🪄 It remains to convert the two received hashes, hash E and hash F, into a single one, the so-called top hash. The final hash is a set of unique characters that contains information about the four original records.
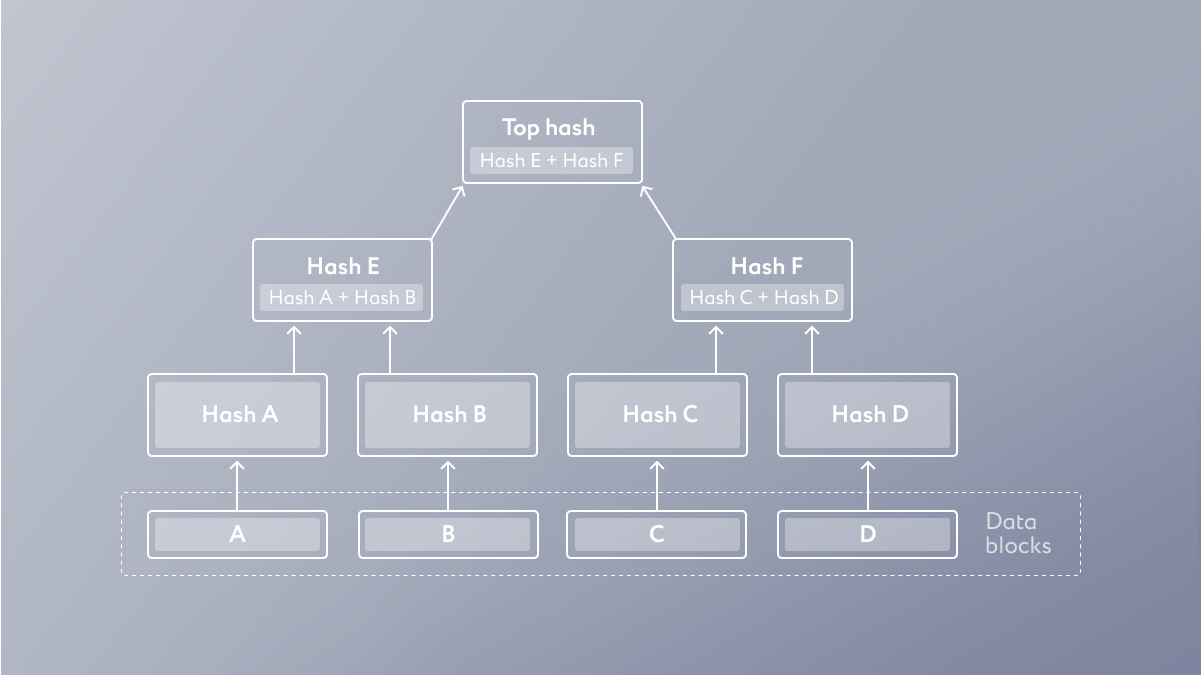
That is how the hash tree scheme looks like.
🔢 Hashing is conducted by special algorithms. For example, the Bitcoin network uses SHA256. It turns any amount of data into a unique set of 64 characters. This is how the first chapter of “The Сatcher in the Rye” by J.D. Salinger looks after hashing via SHA256:
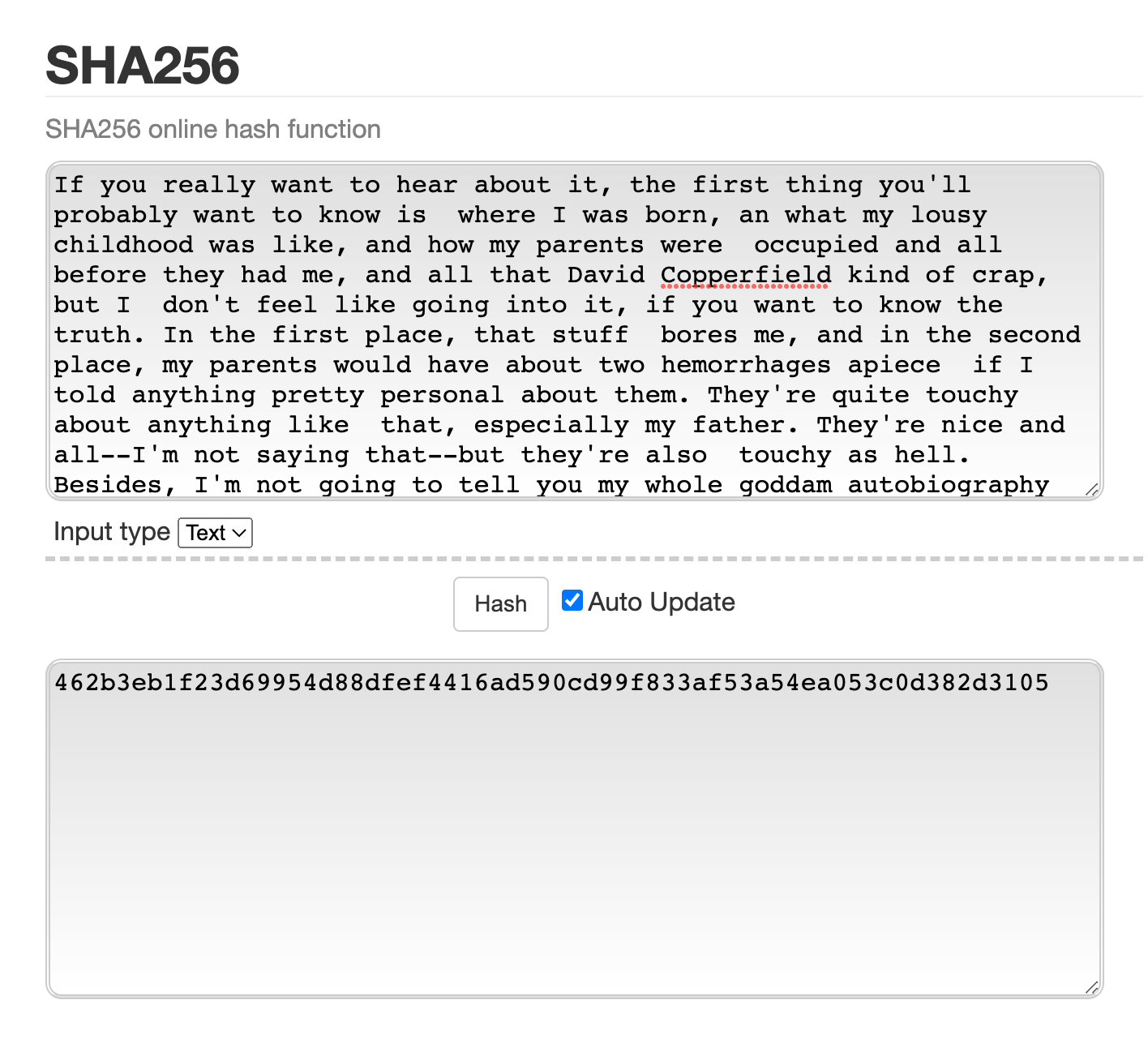
It doesn't matter how long your text is; the system will convert it into 64 unique characters anyway. Check it out.
There are other hashing algorithms, such as SHA-1 and Ethash. They are also based on the idea of a Merkle tree but adjusted with their own rules.
If you know the original text, you can easily convert it to a hash, which is going to be the same for everyone. But if you know only the hash, it is impossible to convert it back to text. This method is used by all modern websites, applications, and services. When you enter a password from your personal account, the site only sees its hash. If it matches the hash stored in the system, you'll get an entrance. And if the site is hacked, then the thief will see only your login and password hash, in other words, useless data. Personal data can still leak, but someone who receives it can't use the information to open an account.
Now back to the "glue" we mentioned before. Let's say we get the first block hash. Now, in order to link it to the next one, the system takes the first hash and includes it in the calculations to form the new block's hash. Here is why this step should be taken:
⚖️ To ensure data validity. If we replace at least one character in any block's data, the system will change further hashes. To find the scam, we should just compare the original blockchain (we already learned that we have plenty of them stored all over the world) with the one that someone tried to fake.
🧚 To reduce the blockchain's size. Hashing helps to save space in blocks due to data compression and streamlining.
🔐 And the last thing that makes blockchain technology effective and that we’ve already discussed: decentralized storage. Term means simultaneous storage of several blockchain copies on different devices all over the world that belong to the project network participants. This approach ensures the reliability and security of data, because scammers can't access enough resources to replace information on all the devices.
Types of blockchain
We have several blockchain classifications. Let's take the British government's one from the "Distributed Ledger Technology: beyond block chain" report. It includes three types of blockchains:
📖 Unpermissioned public ledgers. That is an open public registry so anyone can get the blockchain's copy. An example is bitcoin.
📗 Permissioned public ledgers. Those are closed public registries whose integrity can only be maintained by pre-selected network members. An example is Hyperledger.
📕 Permissioned private ledgers. Those are closed private ledgers with limited access. An example is the closed blockchain systems of three central bank digital currencies (CBDC): the Bahamas Sand Dollar, the Venezuelan Petro, and the Nigerian Digital Naira (eNaira).
What is blockchain consensus
Blockchain cannot work without a consensus algorithm, which is also called a consensus mechanism or a mining algorithm. This is a set of rules for the network workflow that guarantees its security.
Consensus is aimed at coordinating network participants. It regulates the process of adding blocks to the blockchain. It also validates block information through data comparison. Also the algorithm determines exactly who will receive the right to add new blocks for a reward. Network members who add blocks are called validators. They conduct operations using network nodes (equipment with special software).
With the help of consensus, any network member will know exactly what is happening to other participants at any time. It also provides reassurance that everyone plays by the same rules and no one has an advantage over others.
Blockchain consensus mechanisms
There are already many consensus algorithms on the market, and developers continue to reveal new versions on a regular basis. Let's take a look at the popular ones.
🏭 Proof-of-Work (PoW)
In PoW systems, the right to add a block to the cryptocurrency blockchain is given to users with the largest amount of computing power (hashrate) connected to the cryptocurrency network.
Proof-of-Work is considered one of the most secure algorithms. The fact is that the only way to conduct a scam operation in such a system is to conduct a so-called 51% attack. In other words, you need to capture (or increase) computing power until you've got 51% of hashrate. After that, you can set the network rules and assign any coins to yourself. But in the bitcoin case, it is almost impossible because scammers can't reach the required computing power even if they capture supercomputers all over the world. Even if a 51% attack is reached, it can be inefficient: nodes monitoring the operation of the system can recognize and prevent sabotage.
In PoW systems, miners are responsible for issuing cryptocurrencies. They are making computations and taking rewards in coins. Thus, it turns out that the work done by the equipment of the miners backs bitcoin.
Examples of PoW cryptocurrencies: Bitcoin, Dogecoin, and Litecoin.
🍕 Proof-of-Stake (PoS)
The right to add a block to the blockchain in PoS belongs to users with the largest number of coins. PoS systems are faster than PoW, but less secure. Scammers can attack it by turning into the largest holders and waiting for their turn to add a block. But such an attack can be repelled by other system participants.
Proof-of-Stake involves issuance of cryptocurrency through staking,that is holding coins in order to maintain cryptocurrency network stability in exchange for a reward. The reward belongs to validators. You can become one of them on the Ethereum network by blocking 32 ETH in the system.
Examples of PoS cryptocurrencies: Ethereum, Algorand.
🤝 Delegated Proof-of-Stake (DPoS)
Participants who will add new blocks to the blockchain and receive a reward in DPoS systems are chosen by other users through decentralized voting. One coin is one vote.
Since DPoS is related to PoS, the cryptocurrency supply in such systems occurs through staking. The security of such systems is higher than the PoS ones because the right to add a block to the blockchain can only be obtained with trust, which is not easy to get.
DPoS cryptocurrency examples: Hive, Lisk, and Ark.
💾 Equihash
It is related to PoW. This algorithm fights against Asics' dominance on the market. We are talking about professional devices for cryptocurrency mining. Their concentration, according to the Equihash creators, reduces digital asset market decentralization.
The algorithm selects users with regular hardware. The system analyzes the computing power of the devices and their memory.
Equihash cryptocurrency examples: Zcash, Komodo, and Hush.
⛓️ Quark
This is an algorithm with six parallel hashing processes. This approach increases Quark's security against hacks.
Examples of Quark cryptocurrencies: Dimecoin, PlatinumBAR, and AmsterdamCoin.
☁️️ Proof-of-Spacetime (PoSt)
Its principle is similar to PoW. Instead of computing power, the PoSt user provides the cryptocurrency network with access to a certain amount of device memory; therefore, it is considered an eco-friendly PoW option.
Such systems are also used to organize cloud storage, in which participants are rewarded for providing their devices memory.
Example of PoSt cryptocurrencies: Filecoin.
⭐ Proof-of-Authority (PoA)
Its point is to form system participants' ratings with the goal of choosing the most responsible and interested one, who can add a block to the blockchain. PoA is related to PoS.
Examples of PoA cryptocurrencies: VeChain.
🕐 Proof-of-History (PoH)
Its essence is to achieve full clock synchronization on all nodes. In this case, network nodes can work according to a strictly adjusted schedule and check the time between operations.
Examples of PoH cryptocurrencies: Solana.
🔥 Proof-of-Burn (PoB)
It is all about burning cryptocurrencies. Such systems help to maintain the value of assets by deliberately destroying parts of their supply: the fewer coins there are, the more valuable they are.
Examples of PoB cryptocurrencies: Counterparty.
Which algorithm is better?
You should keep in mind that two cryptocurrencies built on the same consensus may perform differently. Digital assets may have additional settings that correct their network rules. For example, Bitcoin and Monero are PoW coins. But it is impossible to mine BTC using a CPU while Monero can be mined with one.
There are many algorithms. Most of them are descendants of the most popular and first PoW and PoS. Each one has its own purpose. For example, in DPoS, developers tried to solve the unfair reward distribution problem using the decentralized voting system. Quark, in turn, tried to improve popular algorithms' security issues.
Most of the leading cryptocurrencies use PoW and PoS. We will not invent anything by saying that the best choice while deciding in which to invest is cryptocurrencies with proven efficient algorithms.
You can buy bitcoin or Ethereum legal and at best price with the European licensed exchange service itez. Before purchasing, learn more about wallet creation.
💌 Telegram, Instagram, Twitter, Facebook
This article is not an investment recommendation. The financial transactions mentioned in the article are not a guide to action. Itez is not responsible for possible risks. The user should independently conduct an analysis on the basis of which it will be possible to draw conclusions and make decisions about making any operations with cryptocurrency.








